Recently I was invited to fix a hacked WordPress site that started displaying a Google warning page as someone visits them. The thing is, the website was hacked for a couple of years, but they did not do anything out of fear of losing all data.
I had volunteered my Friday afternoons with the NGO and after helping out for sometime, we finally managed to have lunch as a team. Midway through lunch, they found out I was working on some WordPress products and told me their problem. And I thought it would be easy.
After lunch, I popped by the office and after a while, FTP-ed into their backend. The hack was massive. Here are the steps I took to fixed the hacked WordPress site.
As a disclaimer, not all WordPress sites are similarly hacked. If it doubt, hire a security expert to work through your site and keep it secure from future hacks. You can contact them here.
Steps to Fix a Hacked WordPress Site
1) Delete all files except for wp-config.php and the wp-content folder
Though I’ve worked on hacked WordPress sites before this, I had never encountered such a heavily hacked WordPress site such as this. As I tried updating the severely updated plugins, I found myself suddenly locked out of admin with WordPress throwing an unusual error.
According to them, the same error kept showing up if they tried to update anything on the site, whereupon they would then contact the host to restore. Browsing through the backend of the site via FTP, I found the core WordPress site compromised, with many core functions overwritten or had malicious pieces of codes hooked into various parts of the site.
In short, the hacker(s) ensured that your site will kick you out of wp-admin the moment you begin updating the severely outdated themes, plugins and core files. That’s why I had to remove them.
2) Look for suspicious files on wp-content
After clearing up a few thousand malware files, I then began going through wp-content. Within the root folder of wp-content were some malware files. And then I discovered that the theme and the plugins were compromised as well.
The hack ensured that if you had just replaced the core WordPress files with a brand new installation, you would get compromised the moment your site went live again.
As such, on compromised sites, its best to replace plugins and themes with the latest version, updated no longer than a year ago. If you have a custom theme and/or plugin, do hire an experienced developer to go through the code line by line, or to rebuild it from scratch.
3) Check the uploads folder
While most WordPress sites don’t mention this, your uploads folder has the chance to be compromised as well. If your site has not been compromised, you can ensure its safety with a .htacess file to prevent access. However, if your website has already been compromised, it is better to go through the various folders on the uploads folder to find out back doors.
In this case, I found a massive hundred sixty thousand malware files on the uploads folder. They had confusing names, but interestingly, they seemed like mini sites that carried out the hacker’s order to hack other outdated sites.
Some of the files were back doors for future exploits.
4) Secure your uploads folder
After clearing up the uploads folder from malicious files, you then need to secure the folder from future infection. This would need a .htaccess file that restricts the folder from executing PHP files. If you are as paranoid as myself, you could even convert JavaScript files in the upload folder to plain text.
5) Scan the database
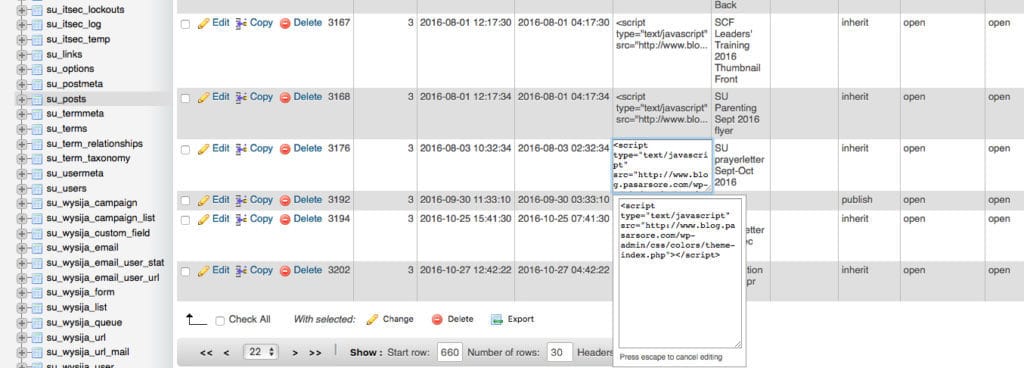
Did you know that your WordPress database could be exploited as well. Here’s where the Exploit Scanner plugin by Donncha O Caoimh comes in handy. With a click of a button, the exploit scanner would go through lines your WordPress installation’s database to find back doors within the database.
According to WPBeginner, hackers can store their bad PHP functions, new administrative accounts, SPAM links, etc in the database.[^1]
However, running the Exploit Scanner plugin might not capture all exploits. Here’s when you need to go through the database tables personally. In this NGO’s website, majority of their posts and pages had a hidden JavaScript line that activated a JavaScript file from another compromised site.
6) Update your server’s PHP to the latest version
If your host runs on an outdated version of PHP, be all means get them to update. After clearing up the site and relaunching it, I found it compromised within days. Fortunately the hackers were trying to load some PHP files on the uploads folder, which already locked down. I got the NGO to contact the hosting company to immediately update the PHP on the server.
If you prefer automated PHP updates and proper security on your hosting, perhaps you could consider WPHostingSpot. I’ve shifted my sites to them and found them really good. Here’s our review of WPHostingSpot.
7) Remove the user called admin
The admin username is one of the first targets for a brute force attack. As WordPress has it’s login page on wp-login.php, most hackers would use their bots to target the admin user to gain admin rights.
And what better than to hammer on the admin username? However, if you remove that username and then install iThemes Security, you can permanently ban hackers who try to hack your site using the admin username.
8) Reset WordPress Salts
You still need a few steps before you can copy over files from the latest WordPress installation over. By resetting WordPress salts, you effectively log any existing users out. This is crucial to prevent hackers from fiddling with the back-end of your site.
9) Reset Passwords everywhere
Passwords are to be reset in a few places, namely the cPanel and for users with the ability to adjust settings on the backend. As for myself, I installed Clef to give an extra layer of security and to prevent brute force attacks for administrator level users.
10) Monitor the site for any future compromises
Finally, you need to monitor the site for any unusual activity. For myself, the combination of Sucuri and VaultPress Premium helps me detect unnatural behaviour as well as potential compromises on a site.
To prevent the site from being outdated again, I installed MainWP’s child plugin so that I could keep the site up to date without spending too much time.
11) Keep backups
While your host might have backups, they might be compromised too. Or your host could unknowingly lose the backups. For sites that value their content and traffic, I would recommend VaultPress Basic, due to the unlimited backups that happen live on an hourly basis.
I can’t emphasise how much time and tears VaultPress has saved me over the years.
Fix a hacked WordPress site : The Conclusion
I can’t emphasise enough how important it is to keep your site updated. If you have problems with being hacked, contact either Sucuri or WPCurve to clear your site of any malicious files. You can find them using the button below
But if possible, buy a license of MainWP and set it to automate the updating of your site. A repairing a hacked WordPress site is time-consuming, frustrating and potentially cause an income loss.
[^1]: http://www.wpbeginner.com/wp-tutorials/how-to-find-a-backdoor-in-a-hacked-wordpress-site-and-fix-it/